TSCM Mastery: Essential Guide to Electronic Surveillance
- Sentry Private Investigators

- Jun 10, 2025
- 15 min read
Updated: Jul 28, 2025
Understanding TSCM Through Real Business Scenarios
Imagine you're in a high-stakes negotiation. You think your strategy is airtight, only to find out your competitor knew your every move beforehand. This isn't a hypothetical. It happened to a UK engineering firm. The culprit? A tiny listening device hidden inside their conference room projector. This is the reality of electronic eavesdropping, and why Technical Surveillance Countermeasures (TSCM) is so vital. TSCM isn't about James Bond; it's about protecting the conversations that drive your business forward.

This image showcases the a piece of equipment used in TSCM, highlighting the technical skill involved in detecting hidden surveillance. The diverse range of tools underscores the need for specialised knowledge and equipment for effective TSCM sweeps.
Electronic eavesdropping has come a long way from simple recorders. Think sophisticated systems capable of transmitting your private conversations across the globe. If your business information is valuable, it's a target. TSCM is your defence against these unseen threats.
The Impact of TSCM on Real Businesses
Just like installing an alarm system or hiring security guards, prioritising TSCM shows you’re serious about protecting your assets. This proactive stance can give you a real competitive advantage. Take, for example, a London law firm that implemented regular TSCM sweeps. The result? Increased client trust and a surge in new business.
Real-world impact: TSCM has saved businesses millions by preventing information leaks and safeguarding competitive advantages.
Building trust: Showing a commitment to security through TSCM builds confidence with clients and partners.
Proactive security: TSCM isn't just about reacting to threats; it's about finding vulnerabilities before they're exploited.
This focus on security built the firm’s reputation for discretion, attracting clients who valued confidentiality above all else. This shows how TSCM provides tangible business benefits beyond simply finding bugs.
Case Studies: TSCM in Action
Let's look at some examples from across the UK:
Manufacturing: A family-owned business in Birmingham was constantly being underbid by competitors. A TSCM sweep uncovered listening devices hidden in their meeting rooms.
Legal: A small Coventry law firm used TSCM to protect sensitive client data during a high-profile case, ensuring a successful outcome.
Tech Startup: A Leicester-based tech startup discovered attempts to steal their intellectual property using hidden cameras and microphones. TSCM intervention prevented a potentially devastating loss.
These aren’t isolated incidents. They highlight a growing trend of businesses recognising the importance of proactive TSCM. Think of TSCM as an insurance policy for your confidential information, protecting you from financial and reputational damage. Investing in professional TSCM services can be the difference between staying ahead and becoming a victim of information theft.
The Modern Landscape of Electronic Surveillance Threats
Think of those clunky gadgets from old spy movies. Today's surveillance devices are nothing like that. They're tiny, often smaller than a dime, and can transmit data for months on a single charge. Hidden in plain sight within everyday objects, they make detection extremely difficult. Talking with TSCM professionals – the people who deal with these devices daily – paints a fascinating picture of this hidden world of corporate espionage.
The Evolution of Eavesdropping Technology
These professionals explain how everyday tech, like smart building systems and Internet of Things (IoT) devices, can be turned into surveillance tools. Even security measures designed to protect you can create vulnerabilities. Imagine a conference room with all the latest smart technology. Seems secure, right? Wrong. It could be broadcasting your confidential meetings to eavesdroppers. TSCM professionals have seen real cases of this, where companies unknowingly compromised their own strategic discussions.
The Psychology of Industrial Espionage
It's crucial to understand why industrial espionage happens. It's a multi-billion-pound industry fuelled by the desire for valuable information. This isn't paranoia; it's recognising the real risks businesses face. TSCM professionals stress that any business with valuable data is a potential target. And the more interconnected our devices become, the more entry points there are for those seeking to exploit them.

The UK Context: Terrorism and Security
Security concerns go beyond just corporate espionage. In the UK, the government regularly publishes statistics on terrorism arrests and outcomes, reflecting the ongoing fight against security threats. These statistics cover operations under the Terrorism Act 2000, including arrests and stop and searches. While specific data on "TSCM" isn't easily found, these broader counter-terrorism measures show the UK's commitment to addressing threats. Discover more insights into UK counter-terrorism statistics
Recognising the Warning Signs
TSCM professionals help businesses spot the subtle signs of potential surveillance. These can be things like unusual patterns in competitor bids (suggesting leaked information), or unexplained knowledge of private conversations. By understanding these indicators, businesses can proactively address potential breaches before real damage is done. Investing in TSCM isn't just about finding bugs; it's about creating a culture of security awareness and protecting the valuable information that fuels business success.
To further illustrate the complexity and diversity of modern surveillance threats, the following table provides a breakdown of common devices encountered by TSCM professionals:
Introducing "Modern Electronic Surveillance Threats by Category," a table offering a comprehensive analysis of the types of surveillance devices TSCM professionals encounter, the challenges in detecting them, and typical scenarios where they're deployed.
Device Category | Detection Complexity | Common Hiding Spots | Transmission Range | Business Risk Level |
|---|---|---|---|---|
Audio Bugs (RF Transmitters) | Moderate | Electrical outlets, furniture, office supplies | Varies greatly; can be up to a mile or more with powerful transmitters | High, as sensitive conversations can be intercepted |
Video Bugs (Hidden Cameras) | High, due to miniaturisation | Smoke detectors, clocks, everyday objects | Dependent on technology; Wi-Fi cameras can have a wide range | Extremely High, compromising visual privacy and security |
GPS Trackers | Moderate | Under vehicles, inside personal belongings | Dependent on network coverage | Moderate to High, depending on the information gained from tracking movements |
Data Interception Devices (Keyloggers, Network Taps) | Very High, requiring specialised equipment | Connected to computer systems, network cables | N/A for key-loggers, localised for network taps | Critical, as sensitive data can be stolen directly |
Smart Devices (Compromised IoT) | High, as they blend in with legitimate devices | Existing smart home or office technology | Dependent on network connectivity | High, exploiting existing infrastructure for surveillance |
Key takeaways from this table include the increasing sophistication of surveillance technology, the difficulty in detecting these devices, and the wide range of potential hiding spots. Understanding these threats is the first step in mitigating the risks they pose.
Inside a Professional TSCM Investigation
Ever wondered how TSCM professionals walk into a seemingly normal office and uncover hidden bugs you’d never spot in a million years? It’s a fascinating blend of cutting-edge tech and good old-fashioned detective work. Let’s take a look behind the curtain of a professional TSCM sweep.
Imagine turning an ordinary office into a controlled environment, a space where even the faintest electronic whisper can be heard. That's the first step. TSCM professionals use specialised equipment designed to pick up on these hidden signals. One key piece of kit is a spectrum analyser. Think of it as an electronic bloodhound, sniffing out the unique radio frequency signatures of hidden transmitters.
Trained TSCM operatives can decipher these complex patterns, identifying unusual blips that might indicate a hidden device. It takes a keen eye to separate the harmless signals from those of a potential eavesdropping device.
Another powerful tool in the TSCM arsenal is thermal imaging. This technology can spot hidden electronics by their heat signatures, even if they're not actively transmitting. It's like having X-ray vision for electronics, especially useful for finding devices tucked away inside walls or furniture. A hidden camera, for example, even when switched off, generates a tiny amount of heat—enough for a thermal camera to pinpoint its location.
Understanding the cybersecurity vulnerabilities within the insurance industry can offer valuable insights into the risks faced by other sectors. It's a good reminder that these threats are widespread. To learn more about these challenges, check out this helpful resource on insurance industry problems.
The TSCM Process: A Step-by-Step Breakdown
A TSCM investigation follows a clear, structured process, ensuring no stone is left unturned:
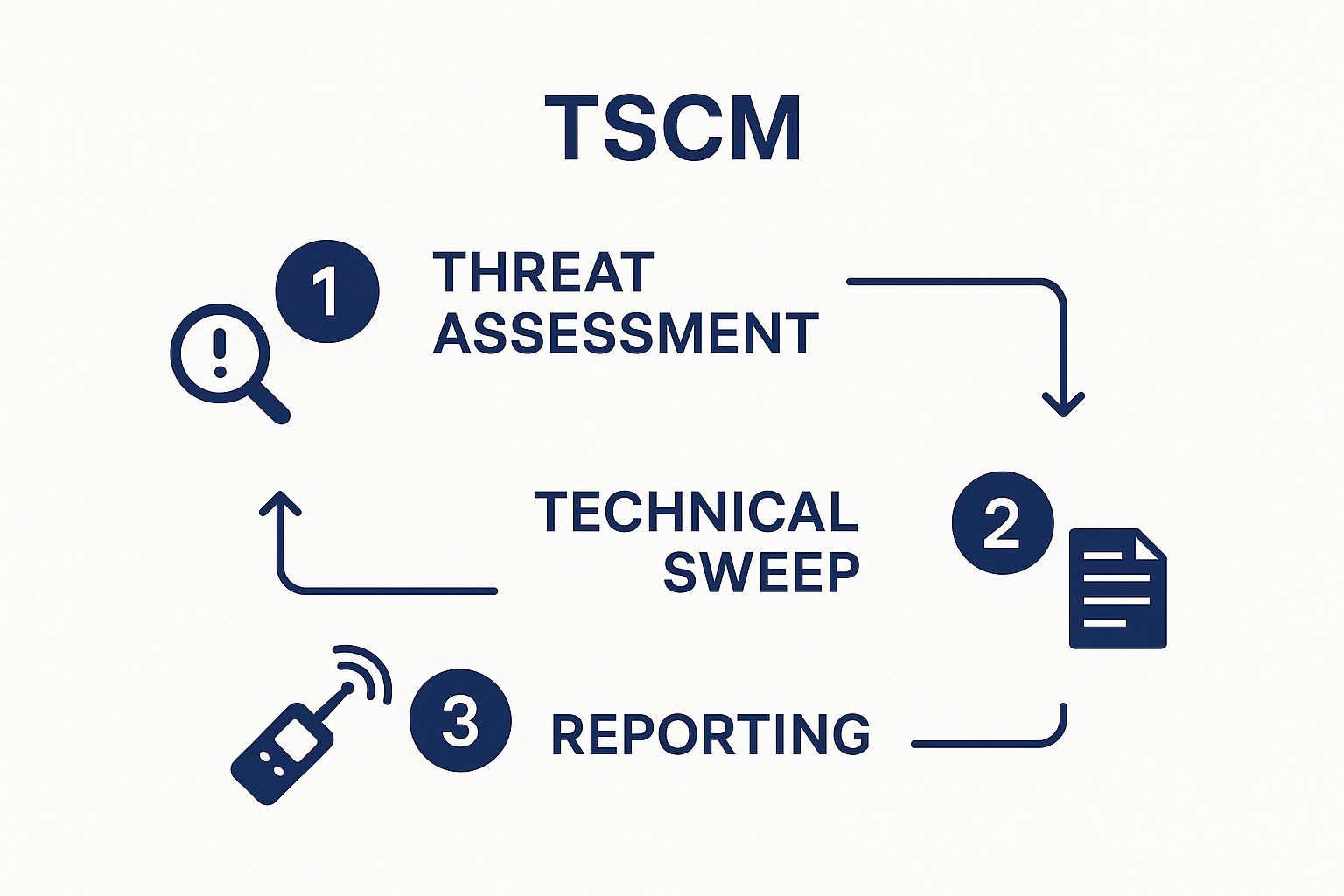
This infographic neatly visualises the three core stages of a TSCM sweep:
Threat Assessment: Identifying potential vulnerabilities and risks.
Technical Sweep: Using specialised equipment to detect any surveillance devices.
Reporting: Providing clients with a comprehensive report detailing the findings and recommended actions.
This methodical approach provides clients with clear, actionable results and a comprehensive understanding of their surveillance risks.
The Importance of Experience in TSCM
While the technology is impressive, the human element is paramount. Interpreting the data from these sophisticated tools requires a depth of experience that only comes with years in the field. A seasoned TSCM professional can read the subtle language of radio frequencies, spot the tell-tale signs of hidden cameras, and differentiate between legitimate electronic activity and the fingerprints of surveillance devices. For a more in-depth look at this, our guide on how to find hidden listening devices offers valuable insights.
The landscape of surveillance technology is constantly changing. It’s a continuous game of cat and mouse, and as surveillance tech evolves, so must the methods of detection. This ongoing evolution is why professional TSCM services are an investment in expertise, not just equipment. A skilled TSCM professional doesn't just find the bugs—they understand how they work and can provide customised solutions for ongoing protection.
Recognising When Your Business Needs TSCM Protection
Technical Surveillance Countermeasures, or TSCM, might bring to mind cloak-and-dagger scenarios of international espionage. But the reality is, TSCM is a practical security measure for businesses of all shapes and sizes, right here in the UK. It's not just for government agencies; from small family businesses to large corporations, the need for TSCM can pop up in unexpected places.

Imagine a family-owned manufacturing company in Birmingham. They were constantly being underbid by competitors, losing contracts they should have won. A TSCM sweep uncovered a hidden problem: listening devices planted in their meeting rooms. Their private business discussions were being leaked to their rivals. Or think about a law firm in London, dealing with highly sensitive client information. Regular TSCM sweeps became a standard part of their security protocol, protecting client confidentiality and their legal strategies.
Real-World Examples of TSCM In Action
These aren’t just isolated incidents. A tech startup in Bristol discovered attempts at industrial espionage, with hidden cameras aimed at their proprietary technology. TSCM intervention prevented a potentially catastrophic loss of intellectual property. These examples show just how many different types of businesses can benefit from TSCM.
Competitive Bidding: Are your competitors consistently underbidding you with uncanny accuracy? This could be a sign of information leaks.
Unexplained Leaks: Has sensitive information mysteriously become public? TSCM can help pinpoint the source of the breach.
Suspicious Activity: Noticed unfamiliar people or unusual activity around your office? These could be red flags indicating surveillance.
These warning signs underscore the need for a proactive security strategy. TSCM isn't about reacting after a breach; it's about preventing it in the first place.
Assessing Your TSCM Needs
Figuring out your business's TSCM needs involves a careful evaluation of your risks. Factors to consider include your industry, the size of your company, how competitive your market is, and the sensitivity of the information you handle. For example, companies in highly competitive industries like finance or technology often need more frequent TSCM sweeps than businesses in less sensitive fields.
To understand more about how these services can protect your business, take a look at our guide on the benefits of a TSCM bug sweep.
From Occasional Sweeps to Ongoing Protection
Some businesses might only need TSCM sweeps occasionally, perhaps before a crucial meeting or during sensitive negotiations. Others, especially those dealing with highly confidential data or operating in high-risk environments, might need ongoing surveillance protection. The best approach depends on your specific situation and risk profile. Talking to other business owners who have already implemented TSCM programs can offer valuable insights and help you decide on the best strategy for your organisation. Ultimately, TSCM is an investment in peace of mind, allowing you to focus on running your business knowing your confidential information is safe.
To help visualise the varying TSCM needs across different sectors, the table below provides a general overview. Keep in mind that these are just examples, and your specific needs will depend on your individual circumstances.
TSCM Risk Assessment Matrix for Different Business Types Strategic analysis of surveillance vulnerability levels and recommended TSCM approaches across various industries and business scenarios
Industry Sector | Threat Probability | Recommended Schedule | Primary Vulnerabilities | Common Attack Vectors |
|---|---|---|---|---|
Law Firms | High | Annual/Before Major Cases | Client Data, Legal Strategies | Hidden Microphones, Network Intrusion |
Tech Startups | Medium-High | Bi-Annual/After Funding Rounds | Intellectual Property, Prototypes | Hidden Cameras, Data Breaches |
Manufacturing | Medium | Annual/Before Product Launches | Trade Secrets, Production Plans | Listening Devices, Competitor Espionage |
Financial Services | High | Quarterly/Before Mergers & Acquisitions | Financial Data, Client Information | Network Hacks, Insider Threats |
Retail | Low-Medium | Annual/During Peak Seasons | Customer Data, Sales Figures | POS System Hacks, Employee Theft |
This table highlights the relationship between the type of business, the likelihood of threats, and the recommended frequency of TSCM sweeps. It also gives examples of potential vulnerabilities and common attack vectors. Remember, consulting with a TSCM professional is the best way to determine your unique needs.
Measuring the True Value of Professional TSCM Services
Think TSCM (Technical Surveillance Countermeasures) is just about finding hidden bugs? Think again. Professional TSCM offers much more than simply sweeping for microphones and cameras. It fundamentally changes how organisations approach sensitive information, building a bedrock of trust and confidence. Talking to businesses across the UK who've implemented TSCM programs reveals a wealth of benefits that go far beyond the sweep itself.
The Ripple Effect of TSCM: Confidence and Strategic Planning
Regular TSCM sweeps create a sense of security that's invaluable for effective strategic planning. Imagine being able to brainstorm, strategise, and negotiate, knowing your confidential discussions truly are confidential. This freedom empowers businesses to take bolder risks, explore more innovative ideas, and ultimately, gain a sharper competitive edge.
For example, one marketing firm in London saw a significant jump in new client acquisitions after implementing regular TSCM sweeps. It wasn't just about protecting existing data; it was about fostering an environment of trust that made potential clients comfortable sharing their vision and building a relationship.
Furthermore, TSCM sends a powerful message to clients: you take their confidentiality seriously. In a world increasingly focused on data breaches and privacy concerns, this commitment to security sets you apart. It can lead to improved client retention and a reputation built on security consciousness.
Beyond Bugs: Uncovering Wider Security Vulnerabilities
What's interesting is how often TSCM sweeps reveal vulnerabilities that extend beyond electronic surveillance. Think weaknesses in physical security, questionable data handling practices, and even concerning employee behaviour. These broader risks, brought to light during a sweep, allow businesses to take a more holistic approach to security, bolstering their overall defences.
In one case, a TSCM sweep at a Birmingham manufacturing facility revealed lax security protocols that gave unauthorised individuals access to sensitive areas. While no listening devices were found, the sweep exposed a critical vulnerability that could have been exploited by competitors or other malicious actors.
Measuring the ROI of TSCM: More Than Just Peace of Mind
Putting a hard number on the ROI of TSCM can be tricky. How do you measure the value of a prevented information leak? But businesses are finding ways. They're tracking metrics like reduced losses of competitive intelligence, increased client retention, and a stronger reputation for security. Some compare the cost of TSCM with the potential damage – financial and reputational – of a major security breach.
The UK's own counter-terrorism efforts offer a relevant parallel. Between 2007 and 2014, 80% of referrals to the Prevent program were deemed false positives. Discover more insights into UK counter-terrorism statistics. This highlights the challenge of identifying genuine security risks and underscores the importance of proactive measures like TSCM. You may also find this insightful: Understanding the Role of a Private Investigator in Modern Cases.
From Optional to Essential: A Shifting Perspective
More and more businesses are recognising that TSCM isn't just a nice-to-have; it's a must-have. They understand that the cost of TSCM is a small price to pay compared to the potential fallout of a successful espionage attempt or a devastating data breach. Investing in professional TSCM services not only protects sensitive information but also cultivates a culture of security awareness that benefits the entire organisation.
Selecting TSCM Professionals Who Deliver Real Protection
Not all TSCM providers are the same. Some possess deep expertise and advanced equipment, while others offer only basic services, potentially missing hidden threats. Choosing the right TSCM professional is the difference between true security and a false sense of safety. This section, informed by industry experts and clients who have navigated the TSCM world, guides you in selecting a provider who offers genuine peace of mind.
Asking the Right Questions: Separating the Experts From the Amateurs
The first step in choosing a TSCM professional is asking detailed questions. Don't hesitate to explore their background, methods, and reporting practices. Here are some key questions to consider:
What TSCM certifications do your technicians have? Look for credentials from respected organisations.
Can you walk me through your TSCM investigation process? A thorough provider will have a systematic approach.
What kind of reporting do you provide after a sweep? A detailed report should outline findings and recommendations.
These questions help distinguish true experts from those offering only basic services. While military or intelligence experience can be helpful, commercial TSCM requires specialised skills.
Evaluating TSCM Equipment: Beyond the Gadgets
Advanced equipment is critical for effective TSCM, but it's just one piece of the puzzle. Knowing how to interpret the data from that equipment is just as important.
This image illustrates the complex nature of TSCM equipment, emphasising the need for specialised training. The various graphs and readings show that simply owning the equipment isn't enough; expertise in interpretation is crucial.
The complexity of these readings highlights the need for highly trained TSCM professionals. A true expert can tell the difference between normal signals and those indicating hidden surveillance devices.
TSCM services offer real, measurable benefits, similar to understanding the impact of marketing investments. It’s valuable to learn about measuring marketing ROI. Just as you analyse marketing ROI, consider how TSCM protects your valuable information and strengthens your business.
Pricing vs. Quality: You Get What You Pay For
While cost is a consideration, be cautious of providers with prices far below the industry average. This could signal subpar equipment or inadequate training. Quality TSCM requires investment in both technology and expertise. Think of TSCM as an investment, not an expense. Consider the potential damage of a successful espionage attempt—lost contracts, reputational harm, and broken client trust. Effective TSCM proactively protects you against these much more expensive consequences.
Building an Ongoing TSCM Relationship: Beyond One-Time Sweeps
One-time sweeps have their place, particularly before important meetings or if you suspect a specific threat. However, a continuing relationship with a TSCM provider offers more comprehensive, ongoing protection. Regular sweeps, combined with security consultations, create a culture of security awareness. This proactive approach helps identify and mitigate threats before they escalate into significant problems. A long-term relationship allows your TSCM provider to learn about your business, understand its unique risks, and adapt to your evolving security needs. This personalised approach is far more effective than a generic, one-size-fits-all sweep.
Adapting to Evolving Threats: Staying Ahead of the Curve
Surveillance technology is constantly evolving. Choose a TSCM provider who invests in ongoing training and remains up-to-date on the latest threats. Ask about their commitment to professional development and how they adapt their methods to counter emerging technologies. Effective TSCM means partnering with a security professional who understands your business and its particular risks, providing true protection, not a false sense of security. It's about building a strong security posture that protects your valuable assets and allows you to operate with confidence.
Key Takeaways for Implementing a TSCM Strategy
Building a robust TSCM (Technical Surveillance Counter Measures) strategy isn't about reacting after a suspected breach. It's about proactively building a fortress around your valuable information. This section offers a practical roadmap, inspired by successful strategies used by UK businesses. We'll explore assessing vulnerabilities, determining the right TSCM frequency, and building a security-conscious culture within your team.
Assessing Your Vulnerability: Where to Begin
Imagine you're securing your home. You wouldn't install the same locks on a garden shed as you would on your front door. Similarly, the first step in TSCM is understanding your unique risks. This means honestly evaluating your vulnerabilities. Think about these key factors:
Industry: Are you in a cutthroat industry like finance or technology, where information is gold?
Company Size: Larger companies often have more complex security needs, like a house with more windows and doors to lock.
Competitive Landscape: Do you have rivals who might play dirty?
Information Sensitivity: What kind of data do you handle? Client data or trade secrets are the crown jewels requiring the highest level of protection.
This assessment helps tailor a TSCM plan that fits your business like a glove.
Determining TSCM Frequency: How Often Is Enough?
Just like regular health checkups, how often you need a TSCM sweep depends on your risk profile. Some businesses might need an annual check-up, while others in high-stakes environments need more frequent monitoring. Think of a law firm dealing with sensitive client data – they might schedule sweeps before big cases, like adding extra security before a valuable delivery. A tech startup, on the other hand, might opt for bi-annual sweeps, particularly after funding rounds, like checking for leaks after expanding the plumbing.
High-Risk: Quarterly or monthly sweeps are recommended for businesses with valuable intellectual property or those in highly competitive sectors.
Medium-Risk: Annual sweeps can be sufficient for businesses with moderate information sensitivity.
Low-Risk: While TSCM benefits all businesses, those with lower risk profiles might consider sweeps every two to three years, or if a specific threat emerges.
Remember, a TSCM professional can provide the most accurate assessment and advice.
Building Internal Security Awareness: Empowering Your Team
TSCM isn’t just about technical sweeps; it’s about building a security-conscious culture. Educating your team about potential threats is like teaching your family fire safety – everyone needs to know what to do. This includes:
Security Protocols: Establish clear rules for handling sensitive information, like locking up important documents.
Policy Development: Create policies that maintain security between professional sweeps, such as guidelines for visitor access and device usage.
Team Awareness: Regularly remind your team about best practices – a gentle nudge, not a constant alarm.
Empowered employees become your first line of defence, like neighbourhood watch for your data.
Integrating TSCM Into Your Security Strategy: A Practical Approach
Implementing TSCM doesn’t need to be complicated. It's like building a house – start with a solid foundation and add layers of protection. Here’s a practical framework:
Baseline Security: Implement basic protocols like strong passwords, access controls, and software updates. This is like locking your doors and windows.
Professional TSCM Services: Schedule a professional sweep to find and address any existing threats. This is like having a security expert inspect your home.
Ongoing Maintenance: Maintain security between sweeps by following protocols and educating your team. This is like regularly checking your locks and alarms.
Regular Reviews: Periodically review your TSCM strategy, adapting to new threats and business needs. Just like upgrading your home security system as needed.
This approach makes TSCM a natural part of your security posture.
Success Metrics, Budget, and Building Relationships
Measuring TSCM success is more than just finding bugs. Think about these metrics:
Reduced Information Leaks: Fewer instances of sensitive data going public.
Improved Client Trust: Greater client confidence in your security measures.
Enhanced Reputation: A stronger reputation for security among clients and competitors.
Budgeting for TSCM varies depending on the frequency and depth of sweeps. Building a relationship with a trusted TSCM provider is like having a reliable security consultant on call – they provide ongoing support, expertise, and tailored solutions as your business grows. They can help you adapt to new threats, offering proactive protection for your valuable information.
Ready to protect your business from hidden threats? Contact Sentry Private Investigators Ltd today for a free consultation and discover how our expert TSCM services can safeguard your valuable information. Learn more about TSCM services at Sentry Private Investigators Ltd



